

Data Security, Battle Readiness
4 Healthcare Provider Organizations' Best Practices
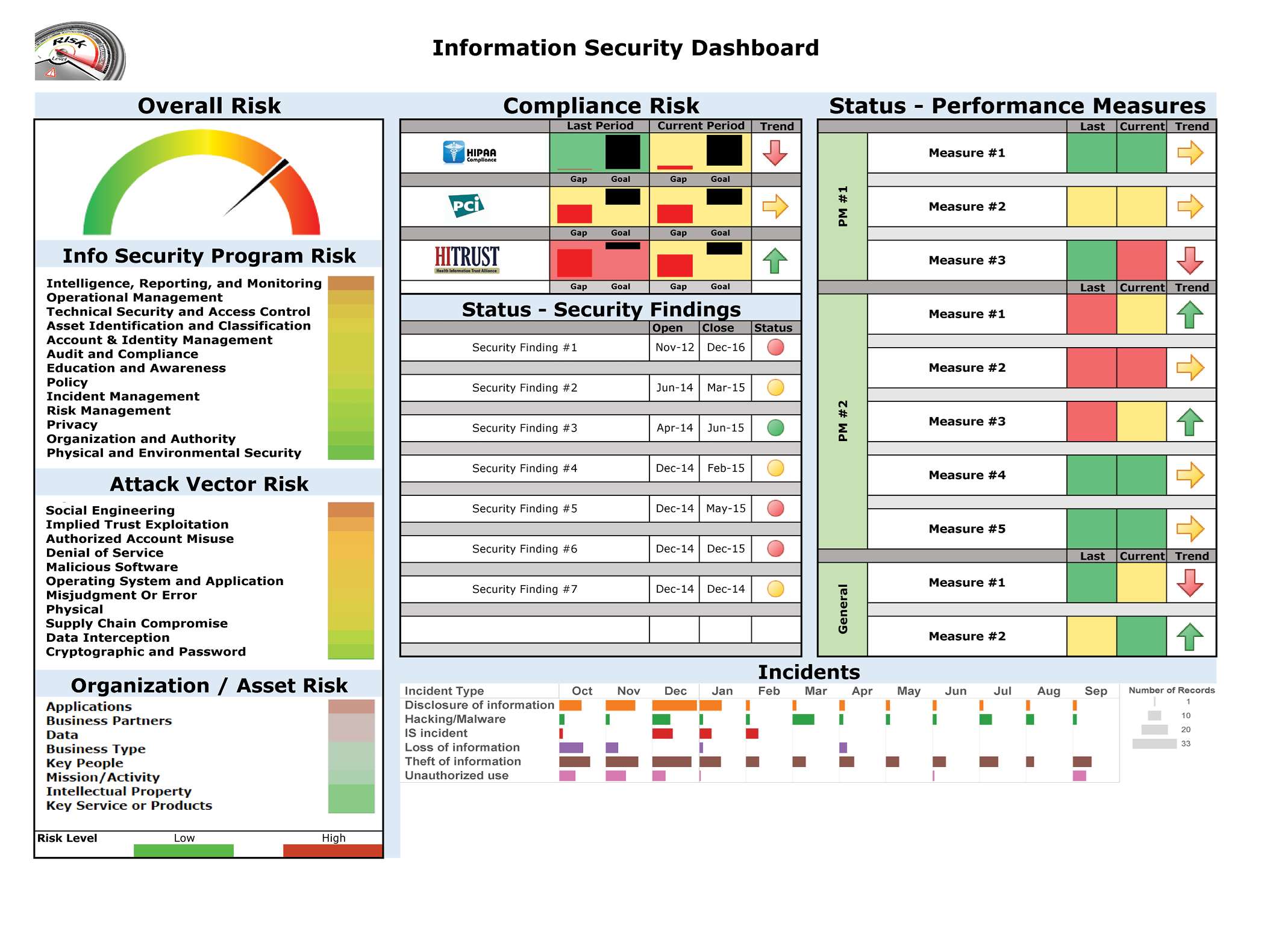
As the rapidly evolving health-data-security landscape becomes increasingly confusing and chaotic, KLAS is embarking on a prolonged research initiative to help providers make sense of the hundreds of tools and services available to them. In August 2015, we will publish our first security perception report, which will include data on over 250 vendors that providers have mentioned during our recent conversations with them. The report will help providers better understand which vendors are being used most and what areas of data security they are being used in. This perception report will be followed over the next 18 months by multiple performance reports, which will discuss what tools and services vendors deliver and how well they perform (see our research areas and report schedule below). We have established an online Security Hub (klasresearch.com/lp/security), which will include a road map for the security reports we intend to publish, our areas of research, the latest security reports, and areas in which healthcare providers can collaborate with us and include their voice in this security research. KLAS recognizes the urgency healthcare providers feel in needing to understand which vendors are out there and how they perform, and we are committed to gathering performance information and publishing our findings with similar urgency. This white paper is a product of that commitment, and as a precursor to our first security report, it highlights several provider organizations that are progressive or unique in how they approach certain aspects of their security. We will continue to work closely with providers to identify crucial areas that are in need of vendor differentiation in this ever-changing industry.
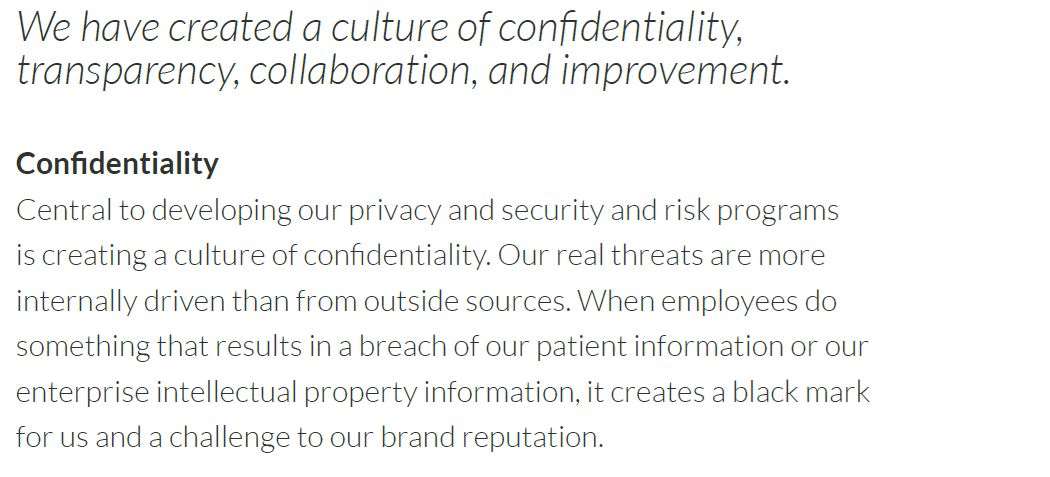
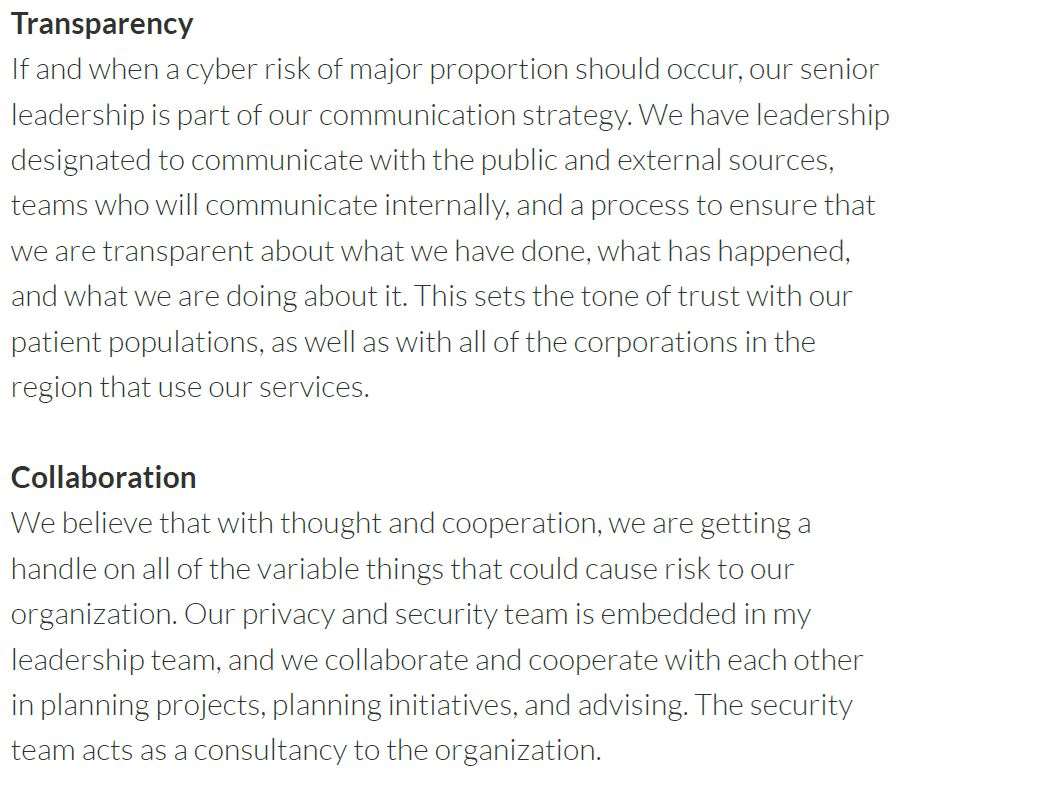
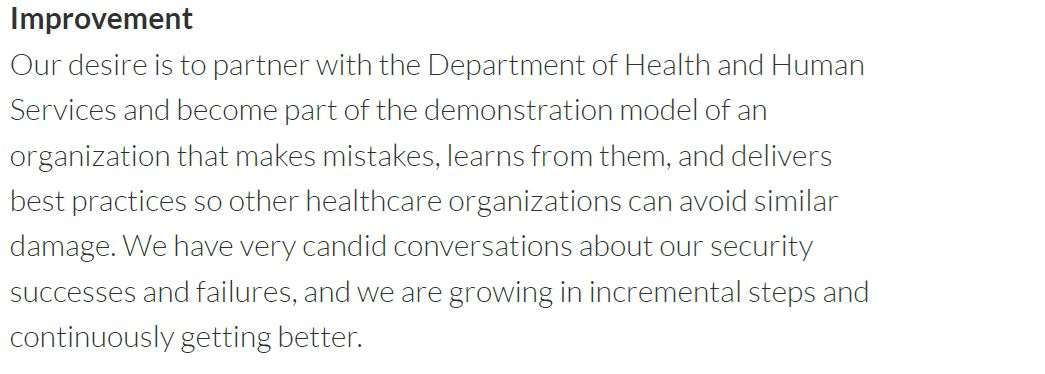
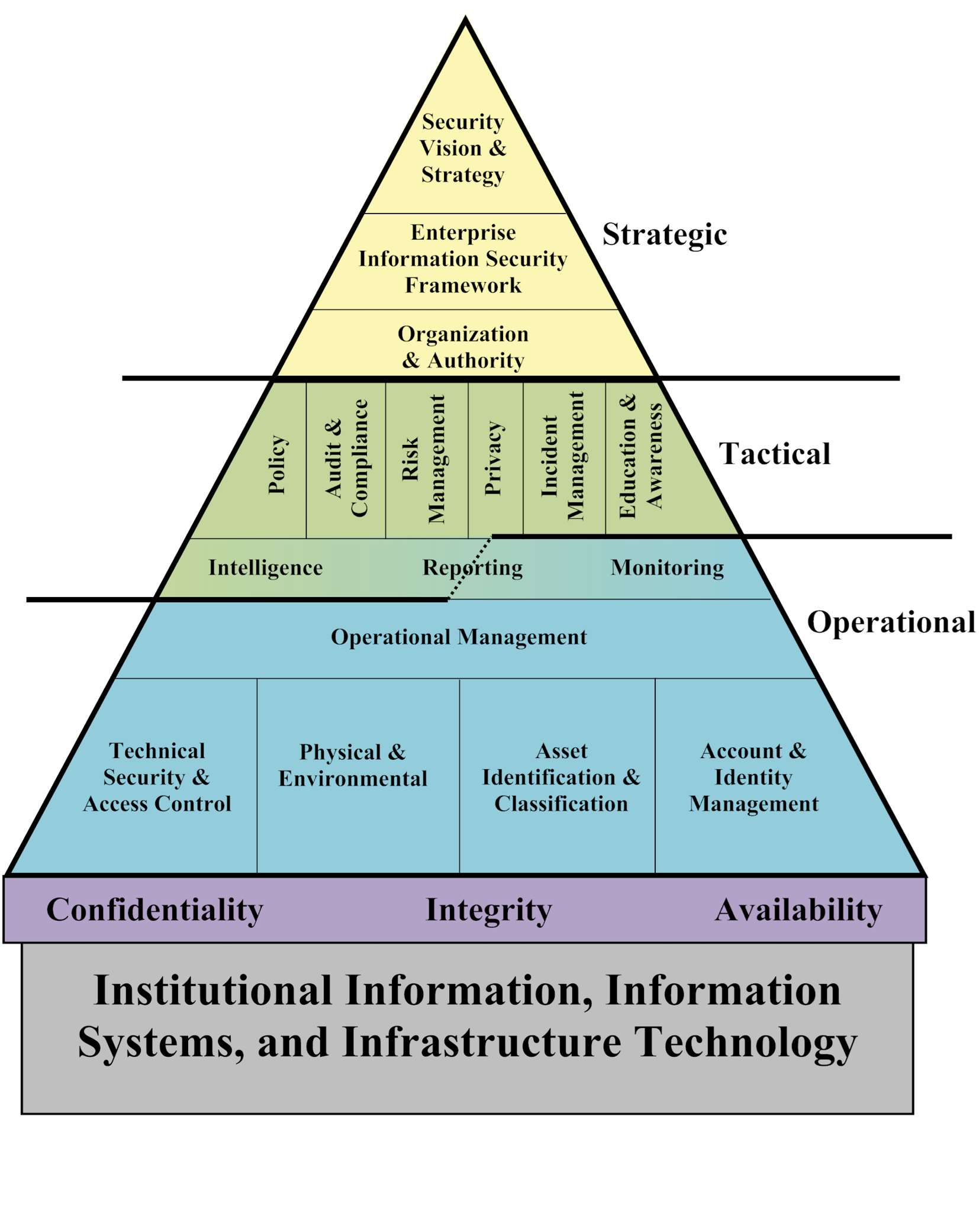
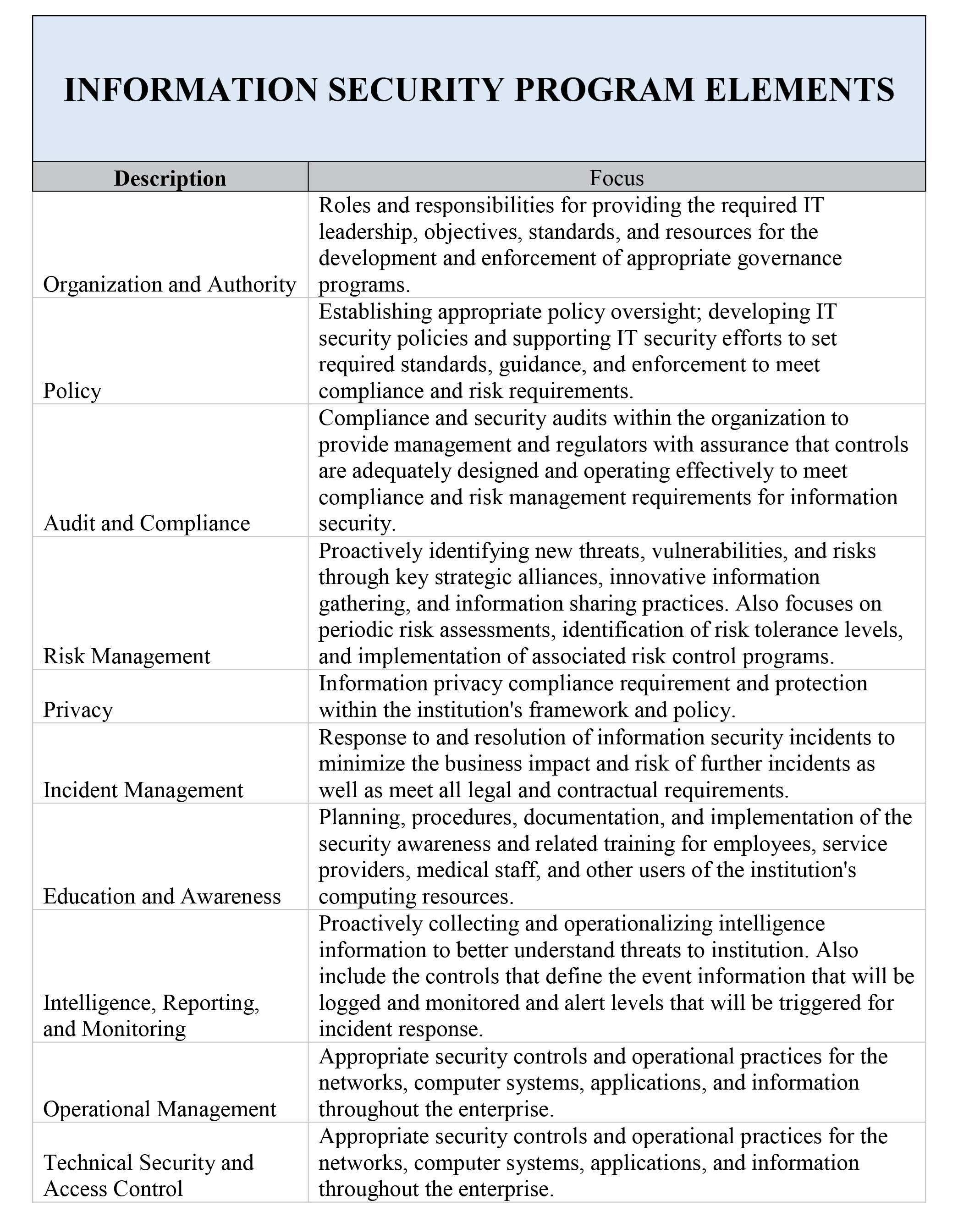
Security Framework | Risk Stratification and Assessments | Education | Culture of Collaboration










This material is copyrighted. Any organization gaining unauthorized access to this report will be liable to compensate KLAS for the full retail price. Please see the KLAS DATA USE POLICY for information regarding use of this report. © 2024 KLAS Research, LLC. All Rights Reserved. NOTE: Performance scores may change significantly when including newly interviewed provider organizations, especially when added to a smaller sample size like in emerging markets with a small number of live clients. The findings presented are not meant to be conclusive data for an entire client base.


